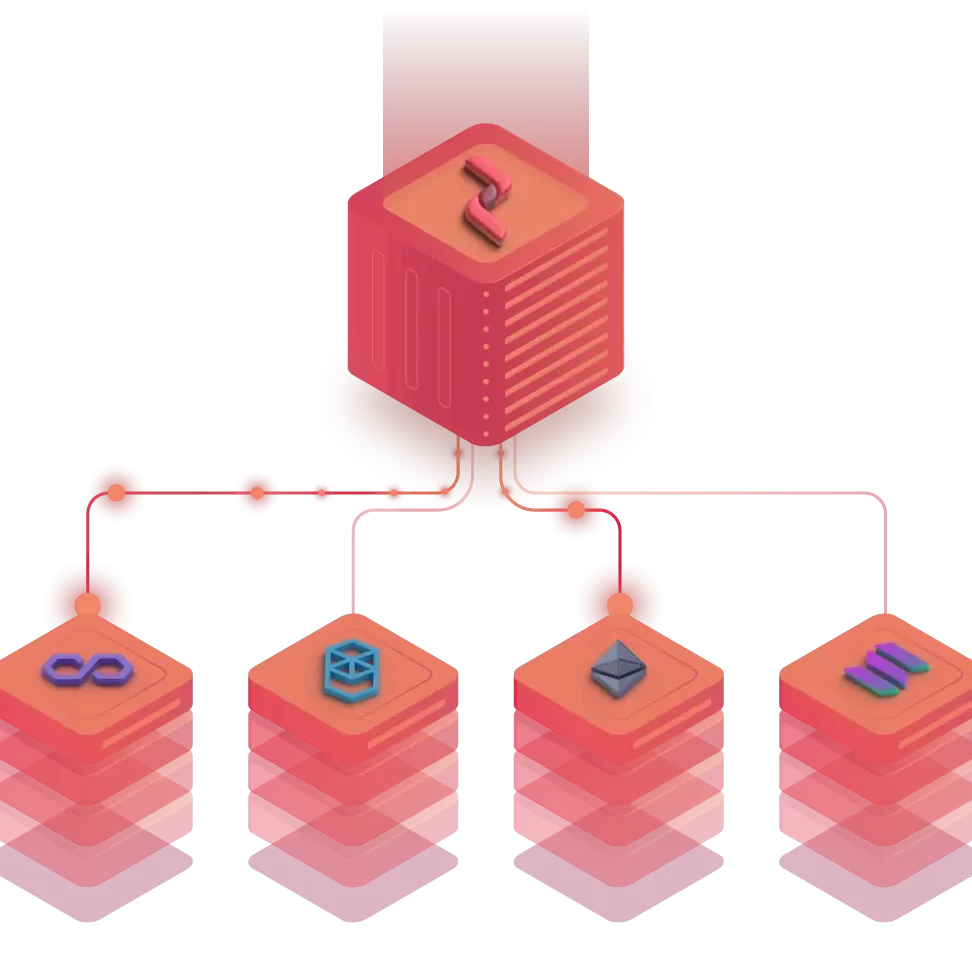
Internet of blockchain: Encrypted database divided amongst several parties that records and stores crypto transactions.
Because of this, you’ll probably want to have antivirus software installed on any computer where you’re using a desktop wallet.
There are several forms of software crypto wallets that you can access on your computer or cellular devices.
Which one is most beneficial for you depends upon your individual situation, but here’s a failure of some typically common types.
Since a hardware wallet isn’t linked to the internet and exists in physical form, it’s considered by many to function as safest solution to store cryptocurrency.
- But establishing your wallet isn’t nearly socking away any Bitcoin or Ethereum you might buy on an exchange.
- Depending on the way the blockchain is used in different applications, it really is divided into public blockchain, private blockchain, and consortium blockchain.
- Scalability is another challenge, as each node can support only a limited amount of transactions.
- To maintain external anonymity, Mixcoin runs on the central mixing server to combine transaction addresses and provide mixing services to users.
Individuals, organizations, machines, and algorithms would freely transact and connect to one another with little friction.
Because they’re limited in size, private blockchains can be very fast and can process transactions much more quickly than public blockchains.
According to Digiconomist, one bitcoin transaction required 708 kilowatt-hours of electricity, the amount the average U.S. household consumed in 24 days.
12 Nodes: Storage And Validation
Where contemporary international money transfers can take up to a few days, exactly the same transaction undertaken over a blockchain network takes only minutes while also being less costly.
It can merge with all the current techniques explained above to attain the privacy objective.
It is just a special sort of encryption where the encrypted data is computed without decryption.
This term was initially introduced by Ronald L. Rivest, Len Adleman and Michael L. Dertouzos in 1978 as a special encryption function called “privacy homomorphism” .
For privacy preservation in cloud storage and computation HE is more suitable for encrypting data.
Thousands of companies are currently researching and developing products and ecosystems that run entirely on the burgeoning technology.
With the increasing number of blockchain systems appearing, even only those that support cryptocurrencies, blockchain interoperability is becoming a subject of major importance.
The objective is to support transferring assets from one blockchain system to some other blockchain system.
Wegner stated that “interoperability is the ability of several software components to cooperate despite differences in language, interface, and execution platform”.
The aim of blockchain interoperability is therefore to aid such cooperation among blockchain systems, despite those forms of differences.
Namecoin is really a cryptocurrency that supports the “.bit” top-level domain .
Always review the amount of support you get, as it can vary greatly with regard to response times and the sort of queries they deal with.
For just one, popular offerings from companies such as for example Ledger and Trezor could be very expensive.
And though losing your wallet isn’t the finish of the world, you will require a recovery seed to regain access to your crypto.
This solution has been developed to improve efficiency over the global food supply ecosystem.
Deng L, Zeng J. Two new identity-based threshold ring signature schemes.
COMPANY verifies the Hash values and digital signature on the certification.
Future Generation Computer Systems
Berenberg, a German bank, believes that blockchain is an “overhyped technology” that has had a lot of “proofs of concept”, but still has major challenges, and very few success stories.
The criminal enterprise Silk Road, which operated on
- In the former, miners are penalized for inputting invalid data by energy, time, and computing power loss.
- Another attempt at addressing the limitations of public and private blockchains, a consortium blockchain is collectively managed by numerous organizations rather than just one.
- Tor, utilized cryptocurrency for payments, a few of which the US federal government has seized through research on the blockchain and forfeiture.
- outputs from nothing.
- Because of this , it’s extremely difficult to manipulate blockchain technology.
(Start to see the exhibit “How Foundational Technologies Take Hold.”) Each quadrant represents a stage of technology development.
The map may also suggest what kind of processes and infrastructure should be established to facilitate the innovation’s adoption.
Managers may use it to assess the state of blockchain development in virtually any industry, as well as to judge strategic investments in their own blockchain capabilities.
TCP/IP unlocked new economic value by dramatically lowering the price of connections.
Similarly, blockchain could dramatically reduce the cost of transactions.
It has the potential to end up being the system of record for all transactions.
As developers create blockchain applications, they should give precedent to securing their blockchain applications and services.
Building security in from the start is crucial to ensuring an effective and secure blockchain application.
Crypto blockchain technology could also be used to create a more secure online identity system.
As increasingly more of our private information becomes available online, it’s important that we have a method to protect it.
Private Blockchains
Different banks can band together and form a consortium, deciding which nodes will validate the transactions.
Research organizations can make an identical model, as can organizations that want to track food.
It’s ideal for supply chains, particularly food and medicine applications.
Trending Topic:
 Market Research Facilities Near Me
Market Research Facilities Near Me  Cfd Flex Vs Cfd Solver
Cfd Flex Vs Cfd Solver  Tucker Carlson Gypsy Apocalypse
Tucker Carlson Gypsy Apocalypse  CNBC Pre Market Futures
CNBC Pre Market Futures  Best Gdp Episode
Best Gdp Episode  Stock market index: Tracker of change in the overall value of a stock market. They can be invested in via index funds.
Stock market index: Tracker of change in the overall value of a stock market. They can be invested in via index funds.  PlushCare: Virtual healthcare platform. Physical and mental health appointments are conducted over smartphone.
PlushCare: Virtual healthcare platform. Physical and mental health appointments are conducted over smartphone.  Mutual Funds With Low Initial Investment
Mutual Funds With Low Initial Investment  Jeff Gural Net Worth
Jeff Gural Net Worth  Robinhood Snacks: Short daily email newsletter published by investment company Robinhood. It rounds up financial news.
Robinhood Snacks: Short daily email newsletter published by investment company Robinhood. It rounds up financial news.